VeraCrypt
$0.00/yearPros
- 256-bit AES, Twofish, Camellia, Serpent & Kuznyechik encryption
- SHA-512, SHA-256, Whirlpool & Streebog hashing algorithms
- Client-Side Encryption & Zero-Knowledge Privacy
- Cascading Encryption Algorithms
- RAM-only storage of encryption keys
- Free encryption software application program
Cons
- No filename encryption
- No built-in cloud storage integration
- Lacks additional features
- Setting up & using the encryption software program is harder
- Online customer support can be improved
VeraCrypt Review
VeraCrypt is an encryption software application program that exists in the cybersecurity market for almost a decade already. As a matter of fact, the VeraCrypt encryption software program has been initially developed by a French-based company called IDRIX on June 13, 2013. The company was founded by a person named Mounir Idrassi and served as the Chief Executive Officer (CEO) of the business organization. There is little information about the identity of Mounir Idrassi which led to certain speculations that are quite unfounded. However, I was still able to find out that IDRIX, the company behind VeraCrypt has currently a registered corporate office at 5 Avenue Ingres, 75016, Paris, France.
While it is true that the encryption software application program has already been rolled out to the public for the last 7 years, there are still lots of things that needs improvement in the encryption system. As a matter of fact, it was only in August 2020 that the developers of VeraCrypt has been able to create and roll out a stable release of the software application program.
Based on my research, VeraCrypt is not entirely original. Most of its code came from an older form of encryption software called the TrueCrypt which has been discontinued in May 2014. Up to this day, the reason why such encryption software application program has been discontinued is still a mystery. Many speculations have actually risen during such point in time. There are rumors wherein possible backdoors created by the National Security Administration (NSA) are soon to be found when independent security audits of the TrueCrypt software were launched in 2014. This could have been one of the many reasons why the TrueCrypt foundation decided to voluntarily shutdown the encryption software application program after a decade of being used.
In connection with this, it is really quite surprising and disappointing at the same time to learn that the TrueCrypt encryption software application program has already been widely used by people all over the world since its initial release in February 2004 before the application program has been shut down. This means that this particular encryption software program is very popular during such period of time.
I also have later found out that TrueCrypt was previously maintained by the TrueCrypt Foundation before the encryption software application program has been abandoned. However, there has been no substantial details about the various people involved in the development and maintenance of the TrueCrypt encryption program. The members of the TrueCrypt foundation is also mostly unknown.
Since TrueCrypt is open-source in nature, conducting independent security audits is very easy. This is the reason why cybersecurity experts were able to produce an independent security audit report for TrueCrypt last September 2015. It was stated in such report that TrueCrypt that there were vulnerabilities found when the Windows installer driver of TrueCrypt is executed in any computer. The first vulnerability involves arbitrary code execution. On the other hand, the second vulnerability and exploit found based on the independent security audit involves privilege escalation through DLL hijacking. These two aforementioned vulnerabilities found on the TrueCrypt encryption program were actually patched by the developers of VeraCrypt.
Aside from that, the developers of VeraCrypt decided to create their own storage format since the storage format of TrueCrypt is too weak in defending itself against possible NSA attacks. Moreover, I would like you to also know that the created storage format of VeraCrypt is incompatible with TrueCrypt. It was designed in such a way that the existing exploits in the TrueCrypt format can’t be used against the VeraCrypt encryption software application program. Based on my research, there are many security improvements that have been made in the VeraCrypt software program over the years. These security improvements will be discussed thoroughly in the Privacy & Security section of the VeraCrypt Review.
I highly suggest that you read the entire VeraCrypt Review to learn more about the encryption software program.
Pricing & Subscription Plans
I’m happy and proud to announce that using VeraCrypt to protect and encrypt all sorts of data and information found on my computer is absolutely free. I really don’t have to pay for anything. However, the developers of VeraCrypt is very open in accepting donations from its users in a voluntary basis. As a matter of fact, there are several ways I can donate in order to ensure that the encryption software program is regularly maintained.
First and foremost, I can actually donate a sum of money to VeraCrypt via PayPal. In order to do this, I need to click the “Donate” menu option found in the main web page of the official website of VeraCrypt. I will be immediately be redirected to a page wherein clickable “Donate” buttons for the benefit of PayPal can be found. I can actually donate in multiple types of currencies. Based on the available “Donate” buttons found on the page, donations in US Dollar, Canadian Dollar, Australian Dollar, Euro, Pound Sterling, Swiss Franc, Japanese Yen, as well as Polish Zloty are accepted.
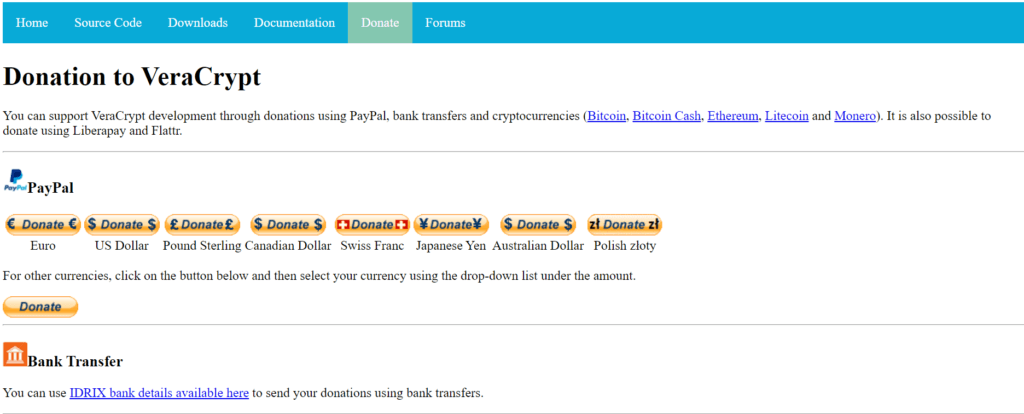
In order to donate using one of the fiat currencies mentioned, I just need to click the “Donate” button corresponding to the type of currency I will be using. Once I do that, I will be immediately redirected to the checkout page of PayPal wherein the payment details are already filled up. I just have to sign in to my PayPal account in order to proceed with the transaction.
There is also another way to donate via PayPal aside from the procedure described above. I can actually click the “Donate” button without any currency symbol just below the multiple clickable buttons with corresponding currency labels. It will redirect me to the checkout page of PayPal wherein I can manually select the type of currency I will be using. Based on my observation, there are currently 25 currencies that are supported by PayPal. After that, I have to click the “Next” button in order to proceed with the transaction. I will then be asked to log-in to my PayPal account to be able to finish the transaction.
As an alternative, I can also use a direct bank transfer in order to facilitate the monetary donation. VeraCrypt compiled a list of banks from various countries wherein sending funds to IDRIX is possible. Currencies supported under direct bank transfer include but is not limited to USD, Euro, GBP, AUD, as well as NZD.
The complete bank details are listed here at https://www.veracrypt.fr/en/Donation_Bank.html.

There are also other donation platforms that I can use. As a matter of fact, both the Liberapay as well as the Flattr platform can be easily used to donate money for the benefit of the VeraCrypt encryption software application program. All I have to do is to click one of the two buttons and select whether to use the Liberapay and Flattr donation platform. On top of that, I was really amazed to find out that I can actually donate money by sending a cryptocurrency. I discovered that Bitcoin, Bitcoin Cash, Ethereum, Litecoin, as well as Monero are accepted.
In order to send one type of cryptocurrency mentioned above, all I have to do is to manually copy and type the crypto wallet address of VeraCrypt corresponding to the cryptocurrency donation option mentioned above. As an alternative, I can just scan one of the Quick Response (QR) codes corresponding to the cryptocurrency I want to donate.
Who is it For?
VeraCrypt is perfect for people who are already knowledgeable with regards to various cybersecurity measures involving various encryption software application programs available in the data security industry. This is very important since the VeraCrypt encryption software application program requires certain amount of technical skills in order to be able to set it up and use it comfortably. Aside from that, I have found out that VeraCrypt is useful for people who wants to have multiple types of data encryption aside from the 256-bit AES.
Aside from that, I have learned that VeraCrypt is perfect fit for people who wants to use various encryption methods simultaneously since cascading encryption is available in this particular software application program.I will discuss all of the encryption algorithms being used by VeraCrypt in full below under the Privacy and Security section of the VeraCrypt Review.
Ease of Use
I have recently discovered that it is easy to download the desktop client version of VeraCrypt to my local computer. All I have to do is to actually click the “Downloads” menu option found in the main web page of the website of VeraCrypt. Once I do that, I will be redirected to a page wherein the downloadable desktop client version installer files for Windows, Mac, as well as Linux computer operating systems will be accessible. Aside from that, installer files for Raspberry Pi as well as FreeBSD operating systems are also available from the same web page.
One thing that I should remember is that I need to select the type of installer file based on the type of computer operating system as well as the type of OS version I’m actually using. This will prevent complications from happening during the installation process for the desktop client version.

Based on my experience, it is too slow to download the desktop client version of VeraCrypt on my local computer. It took me approximately 30 minutes to download the Windows installer file even If I have a relatively fast internet connection. This means that the slow download process might actually be attributed to my current location. I’m currently in the Philippines which is far away from the server of VeraCrypt which is in France. To put things into the right perspective, I still believe that the download process is much faster in countries within Europe and within the American Region.
Once the VeraCrypt software application program is installed in my local computer, I can easily run the program by actually double-clicking the VeraCrypt shortcut icon which was automatically created during the installation process. Once I do that, the graphic user interface of VeraCrypt will immediately appear on my computer screen. The first thing that I need to do is to actually click the “Create Volume” button found in the middle part of the graphic user interface. A secondary application program screen will immediately appear once I do that.

I will then actually be asked how the encrypted volume will be created. I have 3 options to choose from. First, I can actually create an encrypted file container. This type of encrypted volume is the counterpart of an encrypted folder being used by other encryption software application programs in the industry. It is the recommended option for inexperienced users just like you and me.
Second, I can encrypt a non-system partition or an encrypted non-system drive. This option will allow me to encrypt any non-system partition on either a local hard disk drive, SSD, flash drive, or any external hard disk drive. I can make the encrypted volume hidden for security purposes.
Third, I have the option to encrypt the system partition or encrypt the entire system drive. This option is only for advanced users since an entire computer will be locked and encrypted in this type of option. It might actually cause serious problems if I’m not knowledgeable enough in encrypting computer operating systems.

This is the reason why I will actually be selecting the first option. In my case, I will choose the encrypted file container creation option from the 3 choices mentioned above. It is also the easiest to implement as far as I know. After that, I have to click the “Next” button. I will then be redirected to a screen wherein I will be asked whether to create a standard VeraCrypt volume or create a Hidden VeraCrypt volume. In my case, I will be selecting the standard VeraCrypt volume. I need to actually click the “Next” button once again to proceed with the process.
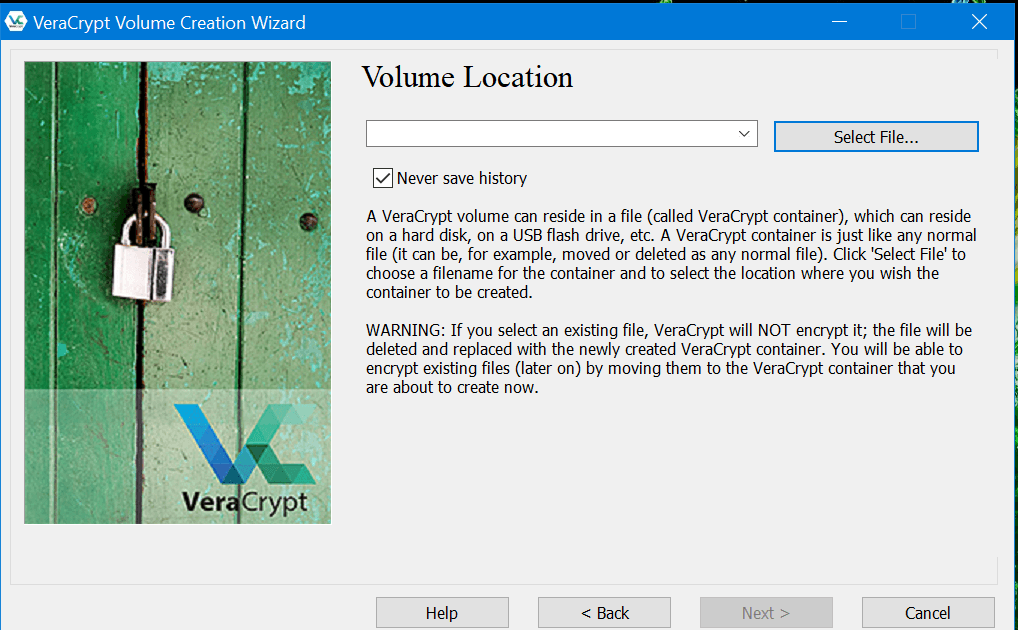
After that, I will be asked regarding the location of the encrypted volume. In order to facilitate the process, I have to click the “Select File” button found at the upper right corner of the graphic user interface of the encryption software program. Once I do that, another screen will appear which will allow me to navigate and specify the file path as well as create a file name.

After I have chosen a file path and a file name, I have to click the “Save” button found on the screen. Once I do that, the blank space provided for the file name in the graphic user interface of VeraCrypt will automatically be filled up. I just need to click the “Next” button again in order to process with the process. As a reminder, I need to make sure that the file name has the “.hc” file name extension.

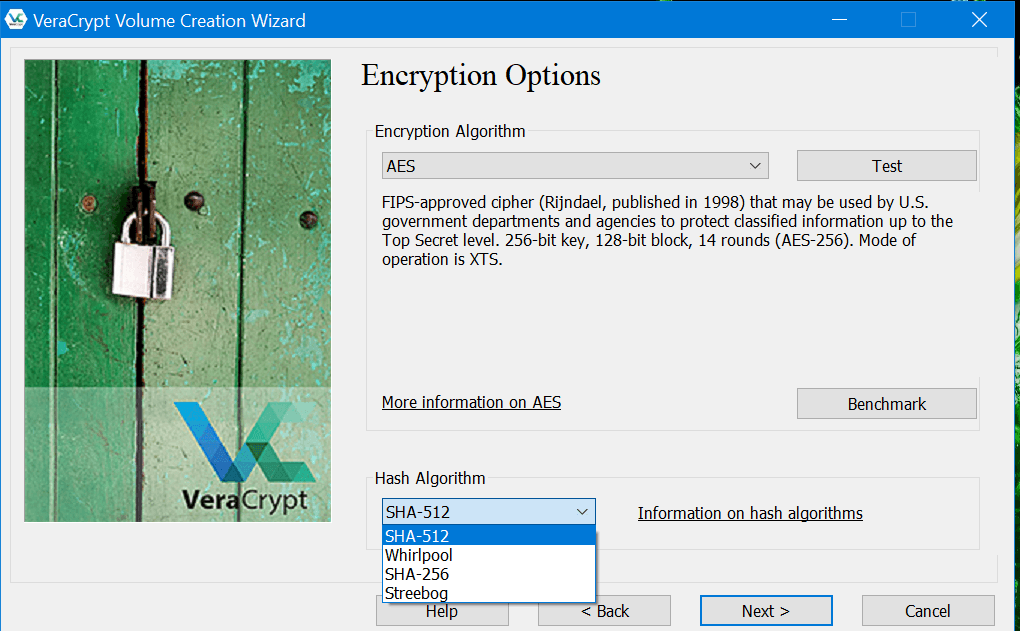
The next step involves the selection of the data encryption algorithm system which will be used by VeraCrypt to protect and secure the encrypted file container. While there are lots of data encryption algorithm systems to choose from the list, I have to select the 256-bit AES encryption. I will also be asked about the type of has algorithm that will be implemented. While there are lots of options from the list, I decided to choose the SHA-512 hash algorithm system. After that, clicking the “Next” button is the best course of action.
I also need to decide about the size of the encrypted volume. I need to specify the size manually by typing it on the space provided on the graphic user interface of VeraCrypt. After clicking the “Next” button again, I will be redirected to a screen within the application program which allows to create a password for my encrypted file container. I need to manually type my newly created password twice and make sure that they actually match.

After that, the screen will display options concerning the encrypted volume format. All I have to in this particular section is to move the mouse of my computer as fast as I can until the status bar regarding the “Randomness collected from mouse movements” are completely filled with a green bar. This will actually be used to optimize the strength of the encryption keys that will be generated by VeraCrypt. After that, I have to click the “Format” button.

Once I do that, the encrypted volume or in this case the encrypted file container will immediately be created.

VeraCrypt navigation buttons include:
- Create Volume
- Volume Properties
- Wipe Cache
- Volume Tools
- Select File
- Select Device
- Mount
- Auto-Mount Devices
- Dismount All
- Exit

Privacy & Security
VeraCrypt uses multiple types of data encryption algorithms. As a matter of fact, AES, Twofish, Camellia, Serpent, as well as the Kuznyechik encryption algorithm are all available. On top of that, I have found out that combing various encryption algorithm programs simultaneously is possible in VeraCrypt. With regards to hashing algorithms, there are also multiple options to choose from. In fact, I was able to discover that SHA-256, SHA-512, Whirlpool, as well as Streebog hashing algorithms are all available. Aside from that, I also recently learned that the encryption keys are stored in the RAM of my computer. This means that every time I restart or shutdown my computer, the encryption keys are totaled wiped off. It basically helps prevent certain kinds of cold boot attacks.

Additional Features
VeraCrypt only has 1 additional feature which I know of. Based on the analysis and encryption system tests that I have conducted, I was able to find out that the cascading use of encryption algorithm systems is possible in VeraCrypt through the XTS mode.
- Cascading Encryption Algorithm
This particular additional feature allows me to implement a data encryption algorithm program which is actually a combination of two or more independent encryption algorithm programs available. As a matter of fact, I can combine AES & Twofish encryption programs to create a stronger encryption cipher. I can also combine Camellia & Kuznyechik encryption programs to strengthen the encryption. The combination of Camellia & Serpent is also possible. On top of that, Kuznyechik & AES can also be mixed together. Moreover, Twofish & Serpent combination is also quite interesting. Serpent-AES encryption can also be implemented as well. Kuznyechik-Twofish combination can become quite surprisingly popular as well.
Aside from the encryption combinations mentioned above, it is also possible to combine 3 data encryption methods all at once. As a matter of fact, AES-Twofish-Serpent combination, Kuznyechik-Serpent-Camellia combination, as well as Serpent-Twofish-AES combination are all available.
Online Support
it is expected that VeraCrypt has relatively weak online customer support system since using this particular encryption software application program is entirely free. Donations are quite rare which means that there is limited funding in order to hire lots of customer support representatives as well improve the level of online customer support that users require.
However, I’m still glad to find out that there is Frequently Asked Questions (FAQs) page available on top of the user manuals and troubleshooting guides. In order to access these materials, I need to click the “Documentation” menu option found in the main web page of the website of VeraCrypt. It will automatically redirect me to a page wherein all of the user guides and FAQ pages will be easily accessible.
I also found out that I can possible contact the developers of this particular encryption software program by sending an e-mail to veracrypt@idrix.fr. As an alternative, I can just create a customer support ticket. There is no guarantee though that the developers will respond in such a timely manner. This is the reason why the developers of VeraCrypt decided to create a forum page instead.
Conclusion
In terms of privacy & security, VeraCrypt is one of the best. It uses multiple data encryption algorithm systems which can further be combined with one another. AES, Twofish, Camellia, Serpent, as well as the Kuznyechik encryption algorithm are all available. Aside from that, I can use this encryption software application program absolutely for free. However, the process of setting up an encrypted volume or an encrypted file container is quite extensive. This means that VeraCrypt is harder to use when compared to other encryption software application programs available. Even if faced with such concern, I still highly recommend VeraCrypt encryption program.
I hope I answered all your questions within this VeraCrypt Review. If you have any more questions, feel free to ask them in the comments section down below!

