
Multi-Factor Authentication System: The Ultimate Guide
As part of being a member of any society, people are always concerned about their right to privacy. They don’t want other people or any organization to look into their quiet private lives that they are currently enjoying. They don’t even want the government to spy on them in whatever form that it could be. As a society, we have bank secrecy laws, data privacy laws, and even anti-wire-tapping laws in various countries across geographical territories in order to protect our inherent right to privacy. This is the reason why multi-factor authentication came into existence. We don’t only want to protect our right to privacy but we also want to enhance the current strength of existing data security.
Because of this, various multi-factor authentication systems have been integrated into various cloud storage systems as well as in the platforms being used by the best cloud backup service providers. This integration process has the purpose and intent of enhancing data security and preserving our right to privacy. This is the reason why we have to discuss multi-factor authentication in its entirety in this particular article.
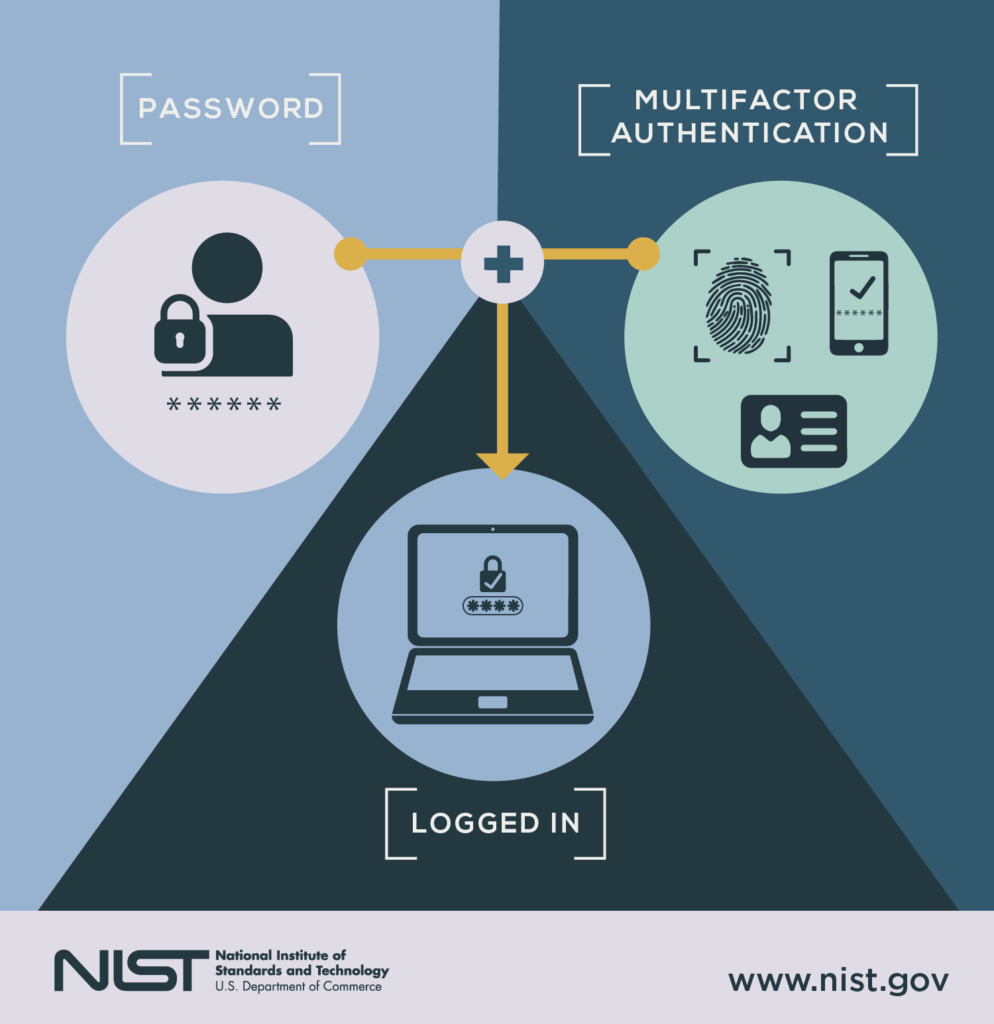
Overview of Multi-factor Authentication System
Many people are asking regarding what the multi-factor authentication system is really all about. To answer that particular question, we can simply state that multi-factor authentication systems are designed in order for a particular person to have access to certain data. It is done by presenting two or more proofs of ownership to the set of data that needs ownership verification.
The process needs the integration of various factors that could unlock a set of data that have been secured multiple times. This means that you need 2 or more keys in order to unlock the said data. The keys to unlock the said data can be a combination of what you possess, what you know, what you are and where you are.
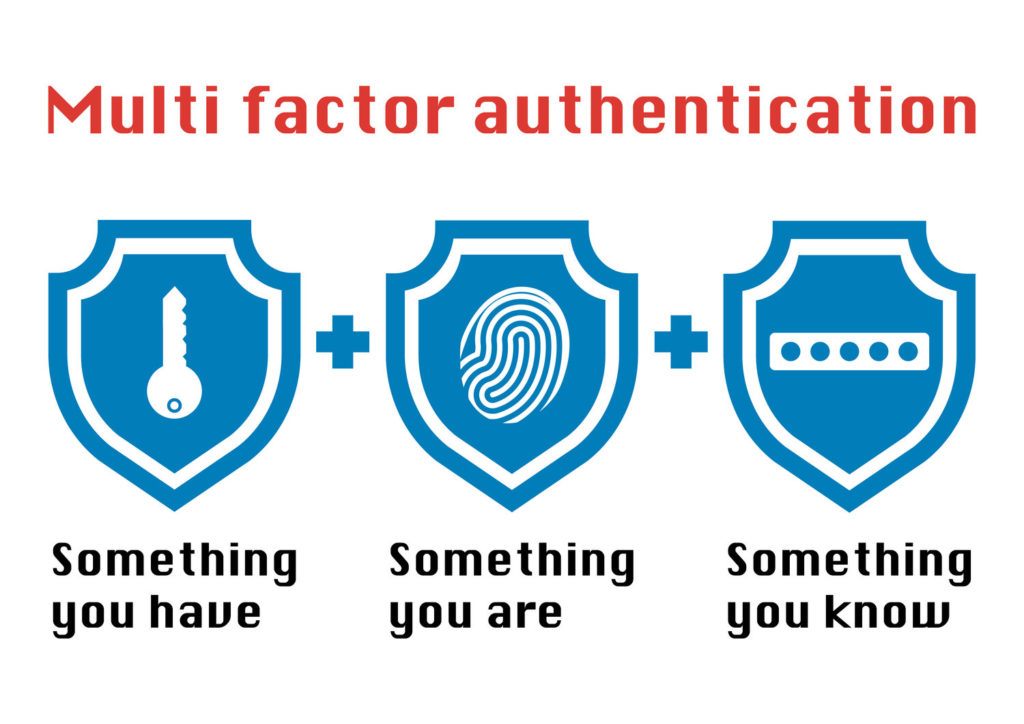
Multi-factor Authentication Key #1: What You Possess
This particular authentication key that could unlock a set of data can be a physical object such as a physical key that could access a drawer or vault where the data is stored. It can also be a physical key such as a USB stick that can be plugged into a computer and generate a specific secret code or token. It can also be a card just like an ATM card in the case of the financial banking system. There are many ways to secure data. Any of these types of keys can be used in a multi-factor authentication system.
It can also be in the form of a security code that you can only access after a particular set of log-in details to an account or a certain password have been discretely typed. These can be done through mobile phones. There are three ways to do that. First and foremost, you can indicate a specific phone number in your account where a secondary code or a one-time password can be sent to you. This particular code is set to expire in 5 minutes or less so that no one would be able to use it in case it falls in the wrong hands.
Second, you can also get the services of two-factor authentication services such as Authy or Google Authenticator. The code usually expires and keeps on changing every minute. So it is mostly impossible to hack the code if you don’t have the possession of a specific phone where the SIM carrying a specific mobile phone number is installed. You can’t also access the data or account if you don’t possess the mobile phone with the installed two-factor code generator or two-factor authentication system.
There are certain cloud storage systems and best online backup service providers that offer a multi-factor authentication system via mobile phones. Click the button to explore and learn more about these online backup service providers.
Multi-factor Authentication Key #2: What You Know
This particular authentication factor is one of the most widely used multi-factor authentication keys in unlocking data or unlocking a particular account. The knowledge factor usually used a combination of letters, numbers and special characters that need to be typed during data retrieval or during the process of accessing a particular secure account. This means that you need to be able to memorize and put the same code or password you have set up in your account or in your computer data storage in order to access it. The password is usually case sensitive. You need to be fully aware of that issue in arranging the lower case and upper case letters of a particular password.
In the case of the financial banking system, it could also be a series of numbers that will serve as a personal identification number or PIN. Aside from that, it can also be three or more sets of questions that have preprogrammed answers. These questions must be very personal to the person accessing the data so that no one else would be able to know about it. It is usually composed of three questions because there are times that answers to the two of the questions can be easily guessed by someone else trying to gain access to the data or account.

Multi-factor Authentication Key #3: What You Are
This particular authentication factor uses the inherent characteristics that can be found in a specific person. These characteristics are deemed unique since no two human beings are exactly the same. The DNA structure of one person is always different from another person. Even if two persons are identical twins, their set of biometric identifiers such as fingerprints, ear shape, retina, iris, voice pattern, typing pattern, physical movement pattern, will never be the same. So in advanced technological data security systems, biometric locks are being implemented. This is the case in the various data centers where sensitive information could be stored.

Multi-factor Authentication Key #4: Where You Are
This particular authentication factor uses the current location of a person accessing data in order to verify whether a person is authorized or not to access it. This is a game-changer since you will literally not be allowed to access data remotely. You can only gain access to a particular set of data if you are inside a secure data storage facility or if you are inside the local area network (LAN) of a particular office or company. This prevents hackers from remotely accessing data that they don’t have the permission to do so.
Advantages of Two-Factor Authentication System
There are several advantages of implementing the two-factor authentication system as a specialized set of multi-factor authentication systems. First and foremost, access codes are constantly changing every minute for two-factor authentication mobile application systems. It is way much safer to use such kind of authentication system than typing a fixed password only. Second, the access code being sent to mobile phones through SMS automatically changes every 5 minutes or less if left unused. Once the right access code has been used and has been typed to recover an account, then it can’t be used again the next time around. You can’t recycle it.
It is also convenient to implement a two-factor authentication system through a mobile phone since the particular object is always being carried around by people most of the time. Mobile phones are also easily accessible to people as well. Aside from that, you don’t have to worry if the access code has already been sent but was delayed in transmission and delivery. In case the access code has been delivered after 3 to 5 minutes and has already expired, then you can always request a new fresh access code easily. So, the slow access code transmission and delivery can be resolved efficiently.

Disadvantages of Two-factor Authentication System
While there are certain benefits and advantages in implementing a two-factor authentication system, there are also possible disadvantages that might arise in the process. First and foremost, a mobile phone used in the two-factor authentication system can actually be accidentally broken and destroyed. Aside from that, a mobile phone which carries a specific SIM connected to the two-factor authentication system can also be stolen. If this happens, then the source of the access code automatically disappears. This is the reason why you have to be cautious in dealing with multi-factor authentication systems such as a two-factor authentication protocol.
There are also cases wherein an access code can be bypassed by an account recovery option. If the person other than the owner of the account tries to recover the data and that person knows every little intimate thing that is deemed private to the account owner, then it can be bypassed easily. Aside from that, with the advancement in technology, SIM cloning is also now possible. If this is the case, then the access code will be sent both on the mobile phone carrying the original SIM card and to the mobile phone carrying the clone of the SIM card. Furthermore, people are still vulnerable to social engineering attacks and phishing which allows hackers to gain access to your private information.
